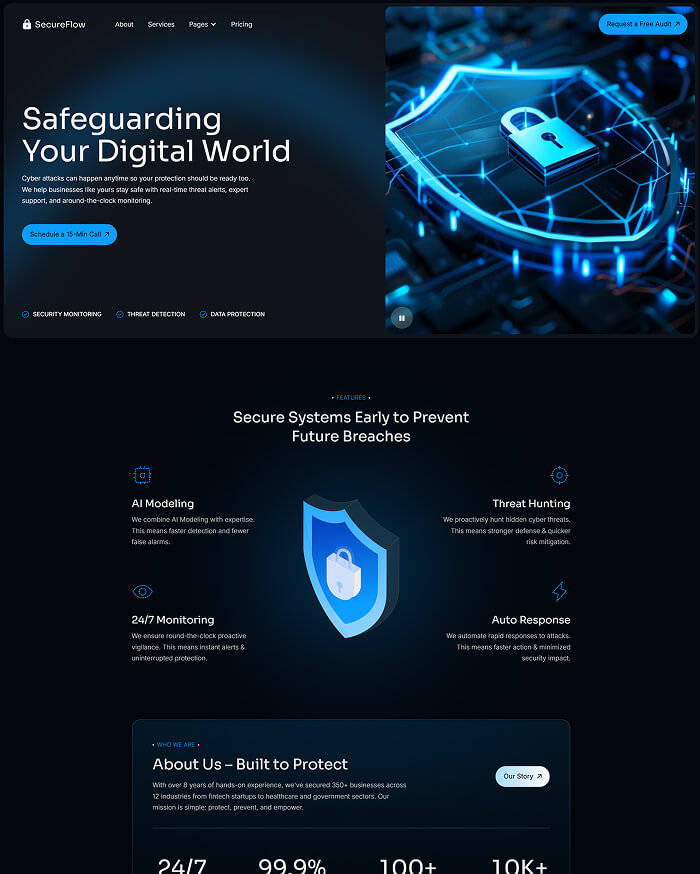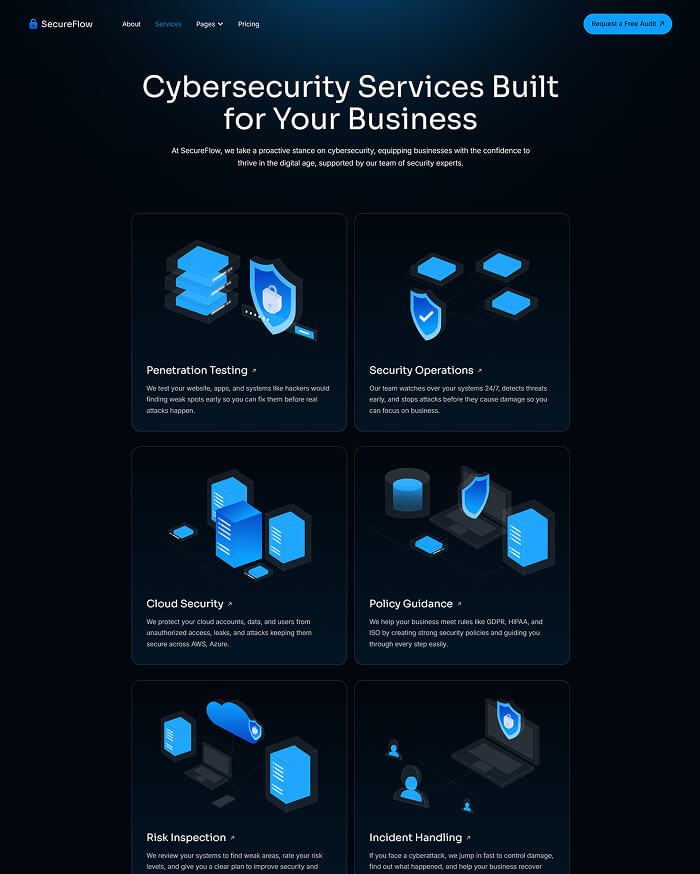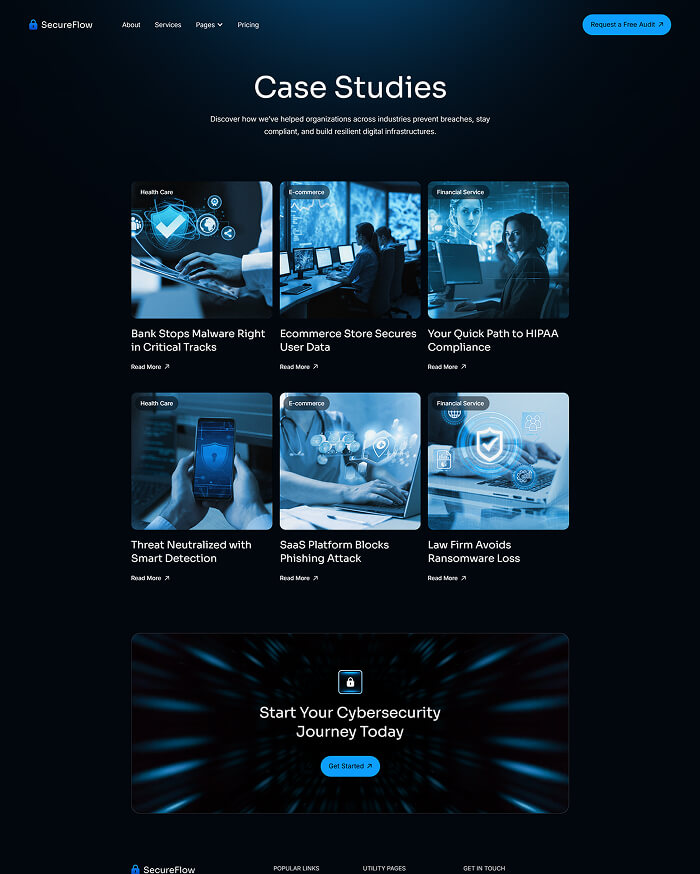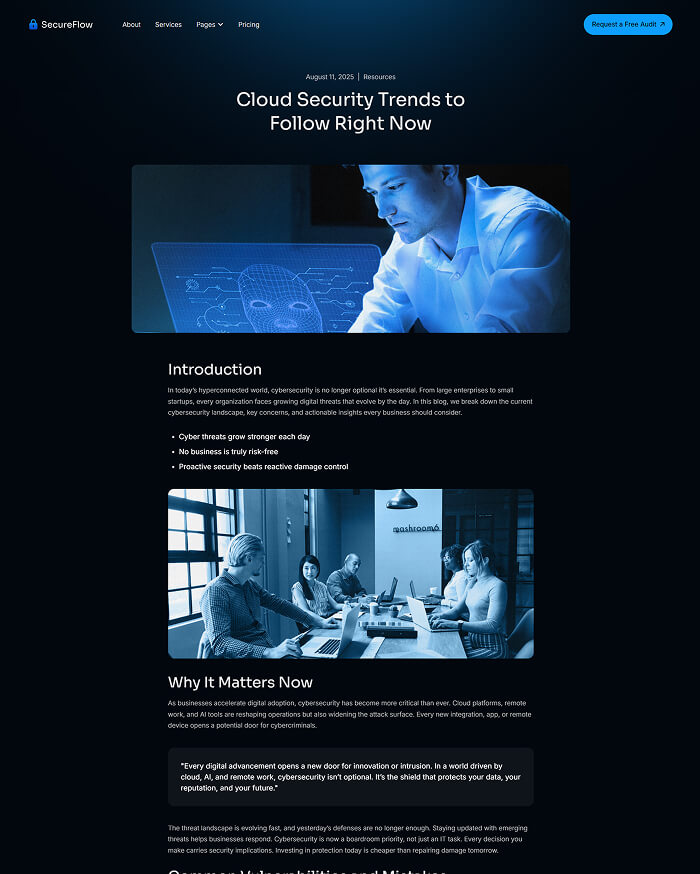
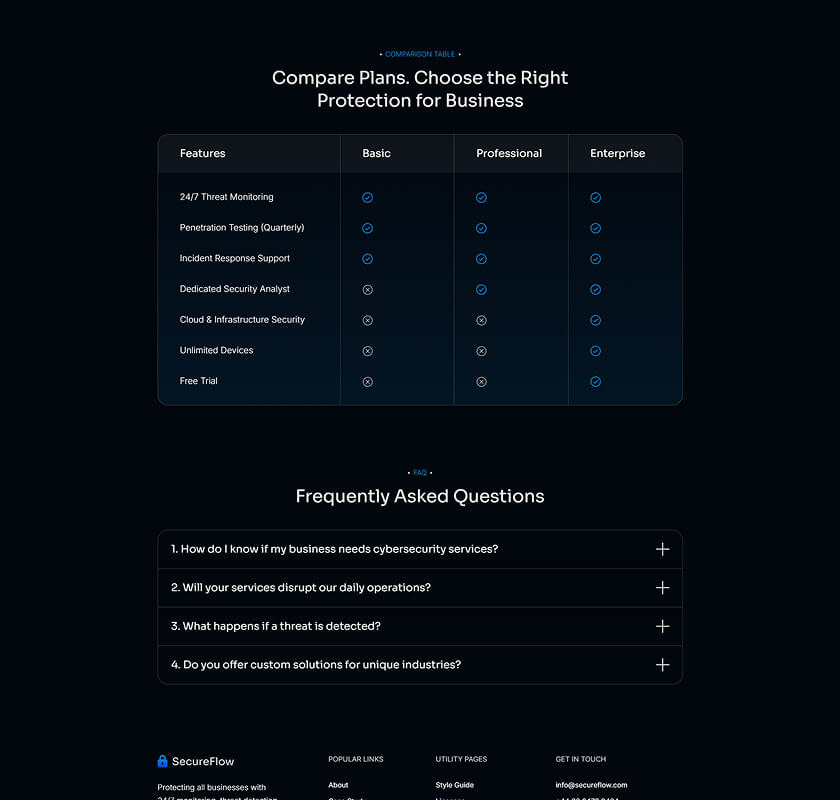
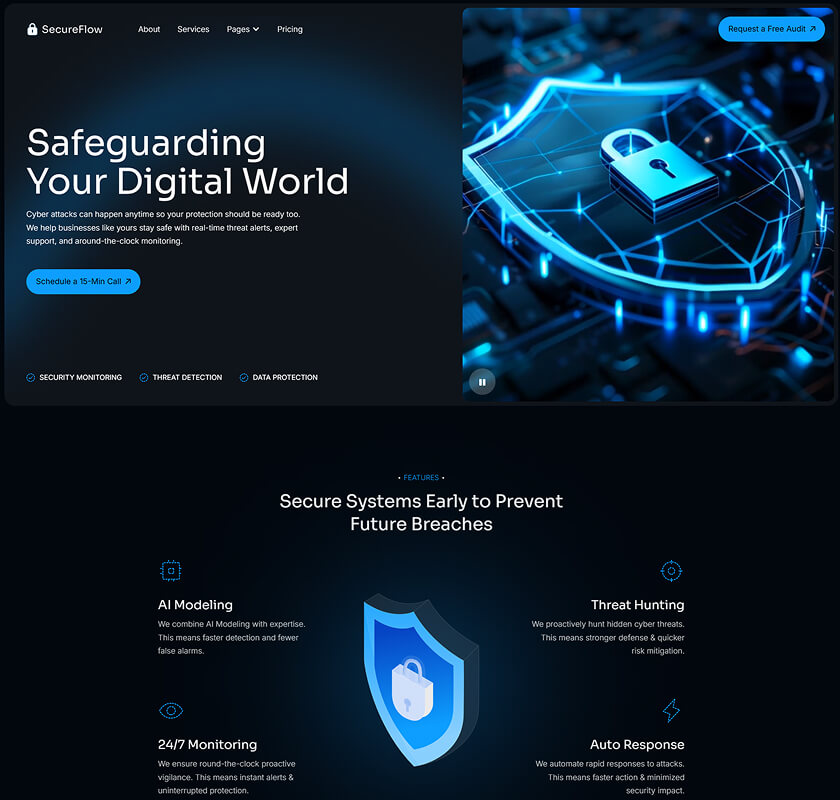
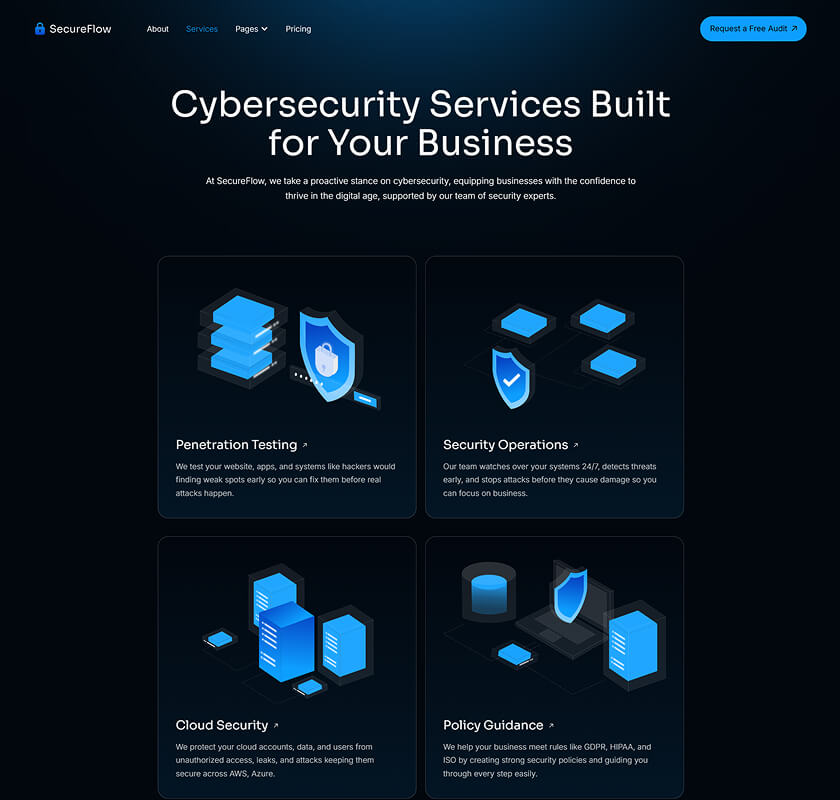
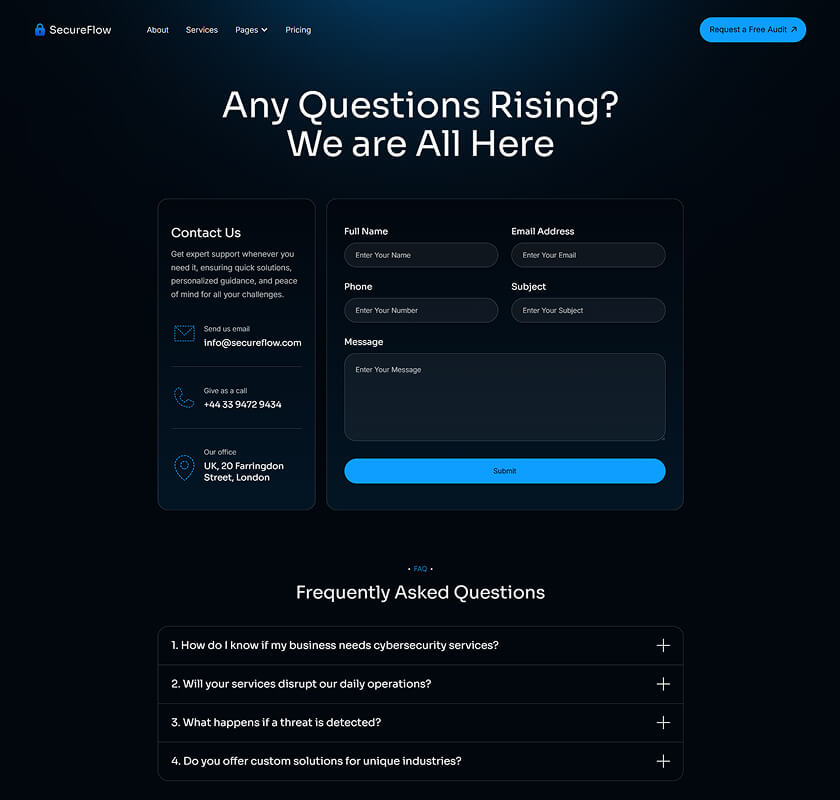











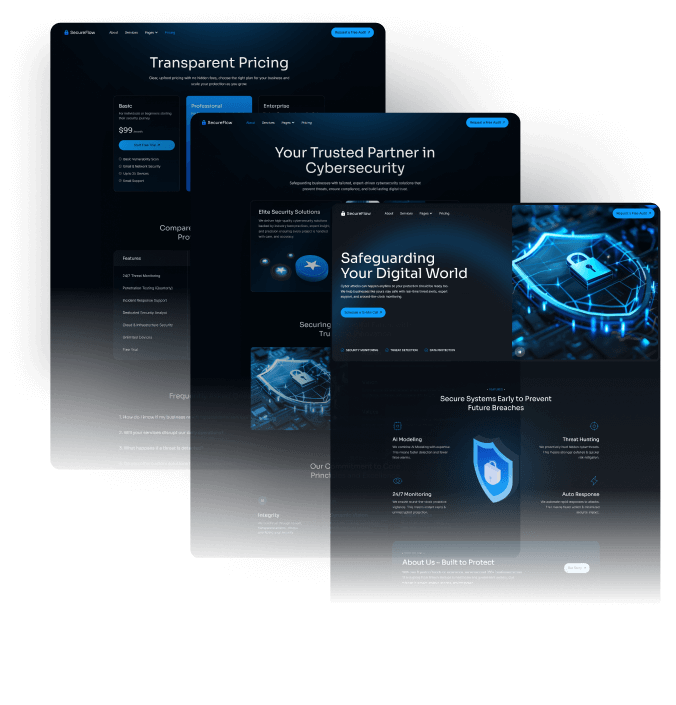
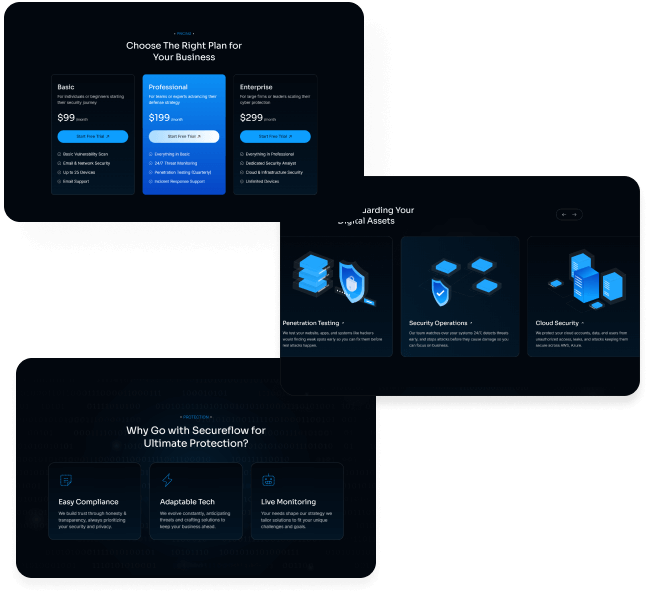
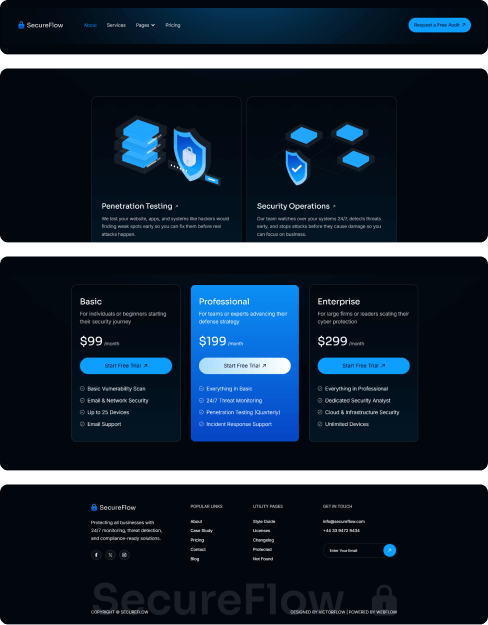
What is included in SecureFlow How many pages, sections, components
12+ Pages
85+ Sections
Components

Figma file included
Contact us with your SecureFlow Webflow template purchase invoice, and we'll provide you with an editable Figma file for your convenience.
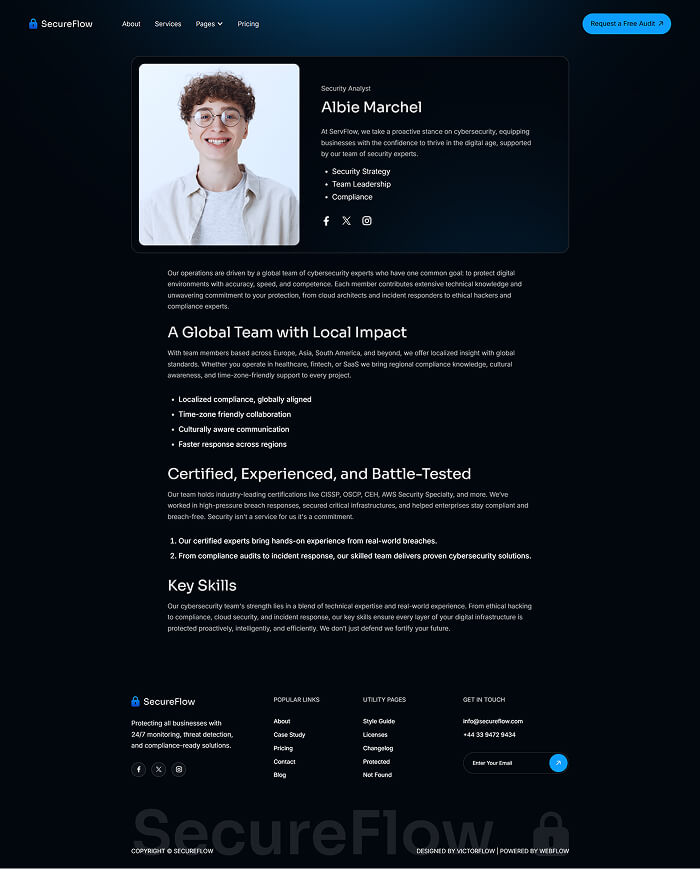
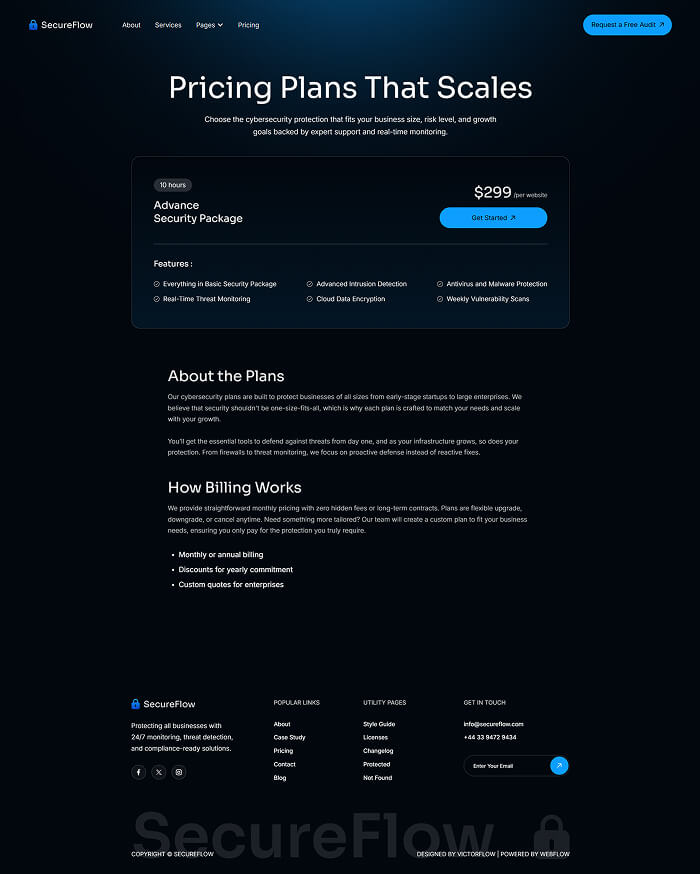
Main pages
Enhance your Extraordinary work techniques with these perfect pages.
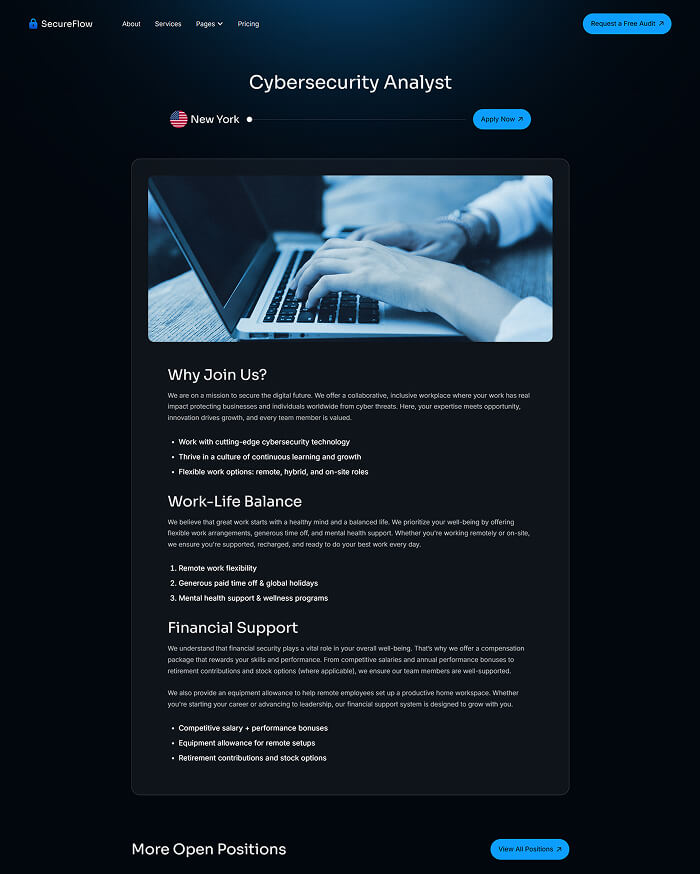
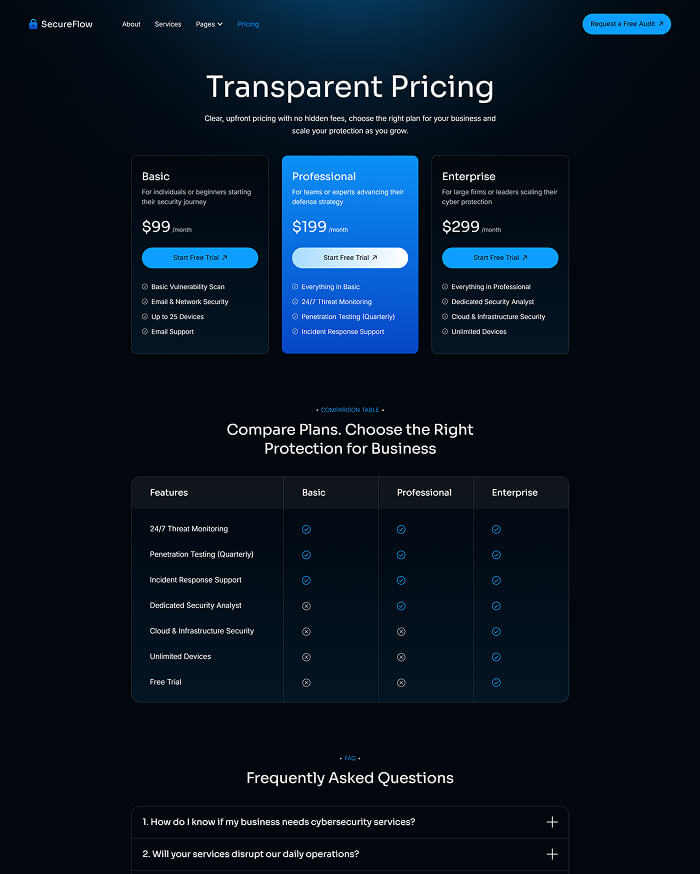
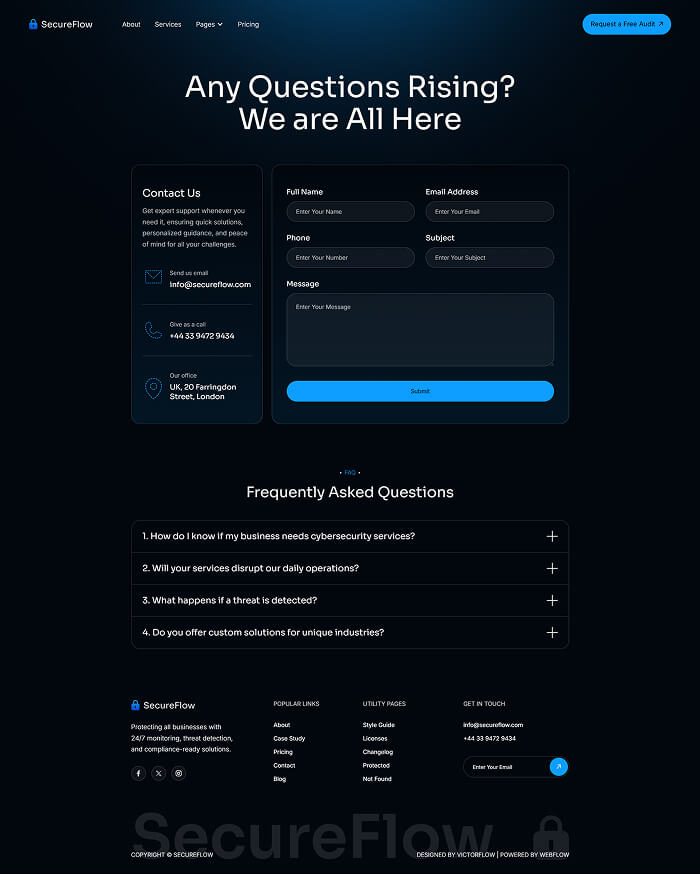
Utility pages
Provide additional functionality and information to users with these pages.
Template designed for your growth & We build everything in standards
Creative template crafted for growth, built with industry standards in mind.
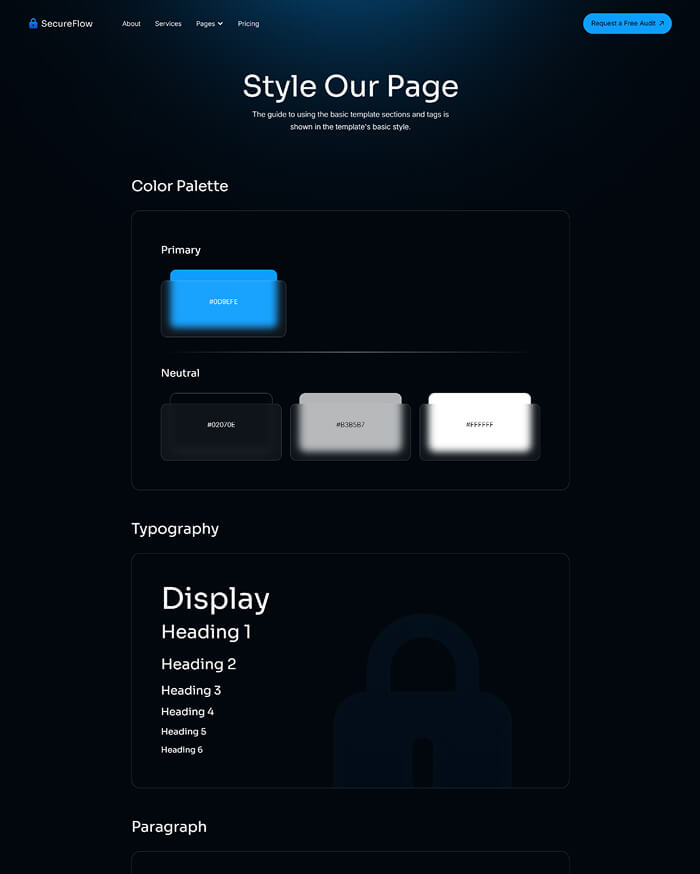
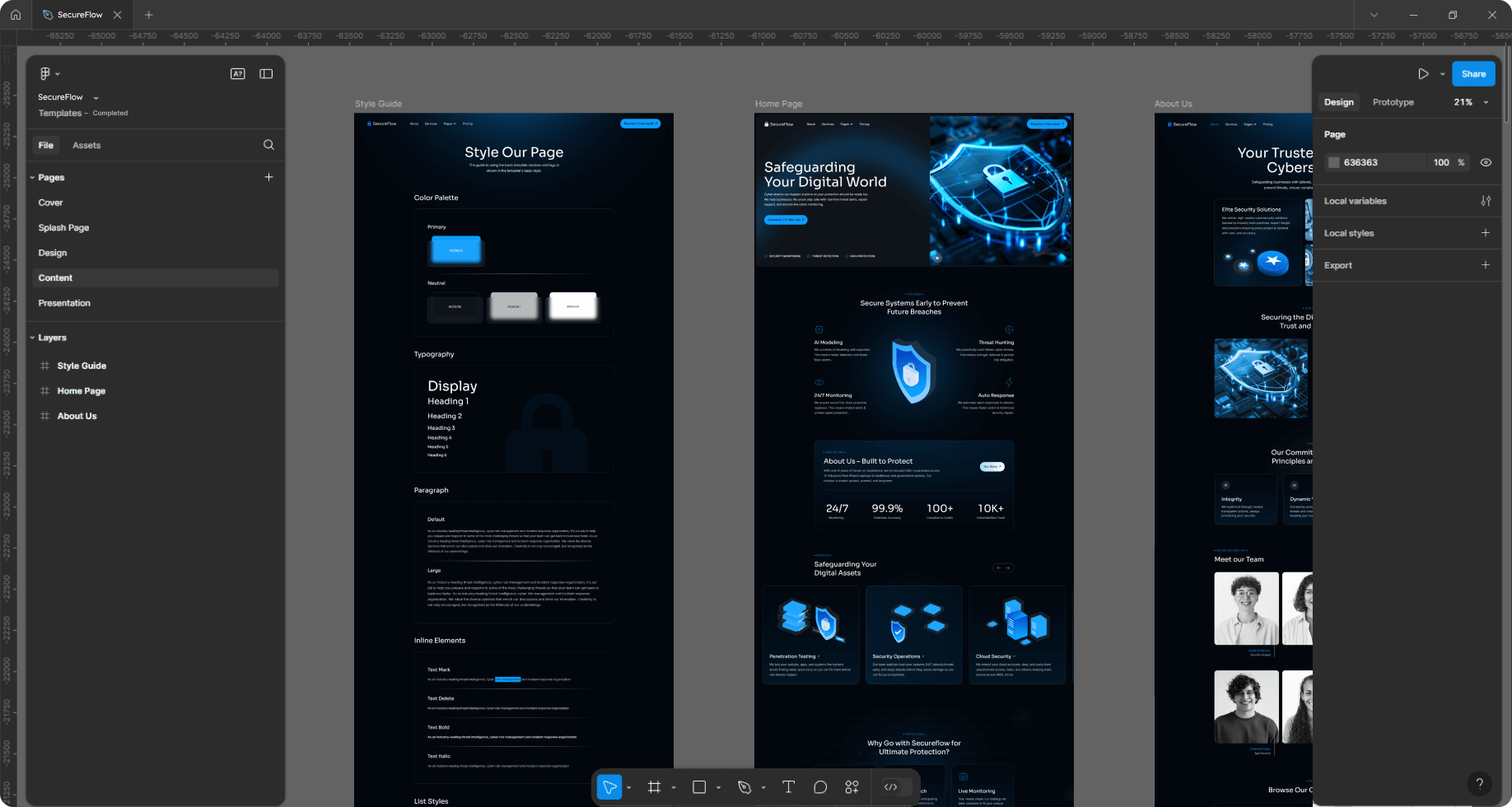
Style-guide
A full-style guide builds consistent, quality writing across all platforms and mediums.
Open Source Fonts
Creative template crafted for growth, built with industry standards in mind.
Open Source Icons
Collaborative, free, and diverse icons for global accessibility and creative initiatives.
Designed on Figma
Crafted perfectly with Figma, An design interface tool that helps to guarantee precision and efficiency in development.

Template marketing section.
Email Signature
Professional touch to email communications and establish the sender's identity & credibility.

Call-To-Action
Banners, or text prompts strategically placed to encourage visitors to take a specific action.
Essential features
This critical, important, and fundamental capability is defined by specific features.
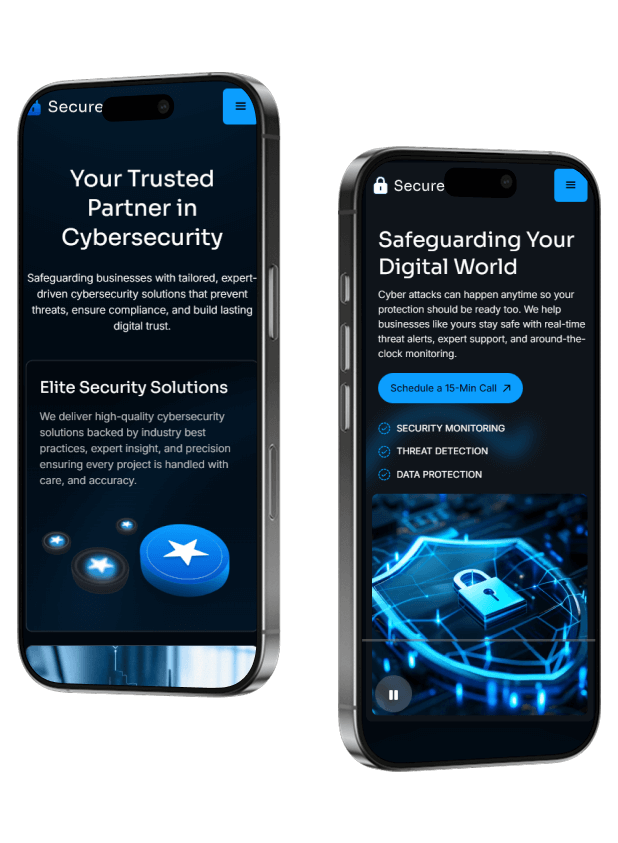
Mobile responsive
Adapts seamlessly to all devices, providing an ideal viewing experience on smartphones, tablets, and computers.
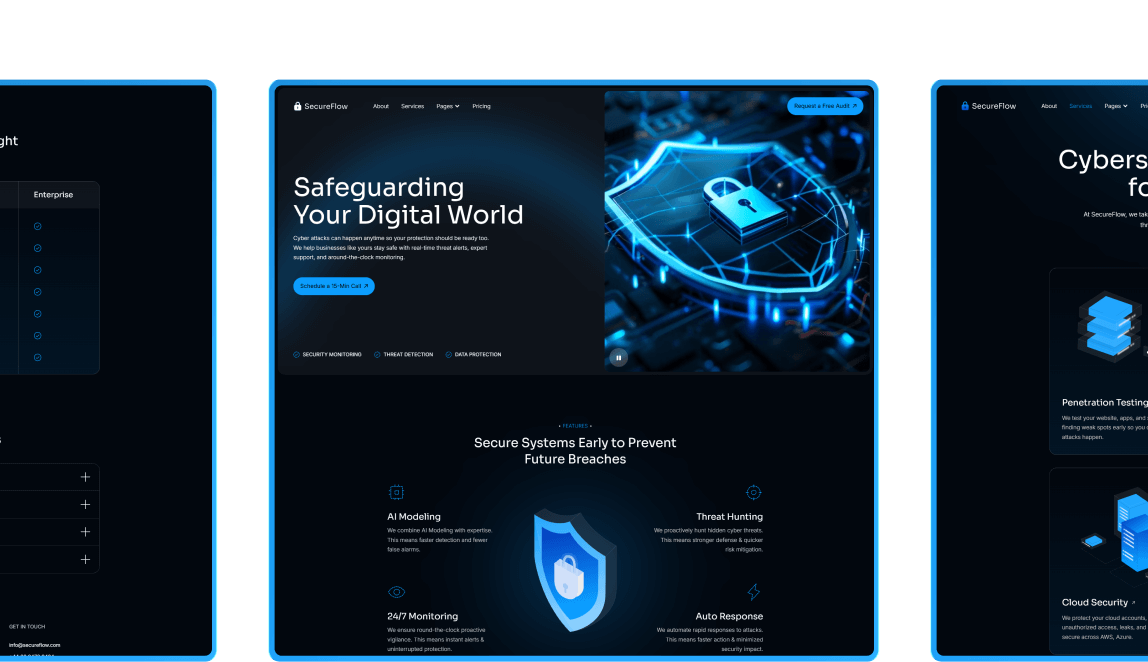
Browse all templates
Templates are precisely designed to offer to your customers delightfully.
Buy now on Webflow
Transform your website with our cutting-edge Webflow Template! Ignite potential, captivate audiences, and elevate your online presence.
Browse our awesome Webflow templates
Explore our amazing collection of Webflow templates, all designed to help you boost your online presence effortlessly.